A penetration test, also known as a pen test or ethical hacking, is a simulation of an attack on a computer system or network to identify security vulnerabilities that could be exploited by malicious hackers. It is conducted to evaluate the security of systems and networks by simulating attacks from both external and internal sources. The goal of a penetration testing exercise is to unveil any weaknesses in the system that can be exploited by attackers to gain unauthorized access or cause harm.
To understand the significance of penetration testing in safeguarding computer systems and networks, it’s important to explore its definition and purpose in greater detail. Penetration testing, often referred to as “pen testing,” is a dynamic security assessment used by organizations to proactively identify and address potential vulnerabilities in their networks. It involves simulating an attack from either an external or internal source by exploiting vulnerabilities in systems or applications. For more information about penetration test, you can read through this link, https://www.nettitude.com/sg/penetration-testing/pen-testing/. Penetration testing aims to assess the security posture of the organization and uncover any areas of weakness that could be exploited by malicious entities.
Types of Penetration Testing
Penetration testing, also known as pen testing, plays a critical role in the security process of any organization. It is a comprehensive security assessment that evaluates the effectiveness of an organization’s existing security measures by simulating real-world attacks. It is essential to understand the different types of penetration tests and their respective roles to appreciate their significance fully.
Network Penetration Testing
A network penetration test is designed to identify vulnerabilities within an organization’s external and internal networks. During this test, the pentester examines weaknesses in firewalls, routers, switches, wireless networks, and other network devices that could be exploited by malicious individuals or groups. Network penetration testing assists organizations in detecting misconfigured devices or services that can serve as entry points into their systems. Additionally, these tests help identify weaknesses in authentication protocols or encryption schemes that could lead to data compromise if left unchecked.
Application Penetration Testing
Application penetration testing focuses on uncovering exploitable flaws within web applications and other software programs developed by the organization itself or third-party vendors. These tests are often more detailed and meticulous than network penetration tests, as they scrutinize each line of code within a program in search of potential backdoors or vulnerabilities that can be easily exploited by attackers.
Benefits of Penetration Testing
Penetration testing, also known as pen testing or ethical hacking, is a cybersecurity practice that involves simulating attacks against IT systems to detect vulnerabilities and assess the security of an organization’s network. Its popularity has grown significantly in recent years due to the surge in cybercrime and data breaches. Let’s explore the benefits of penetration testing and why organizations should consider investing in this service.
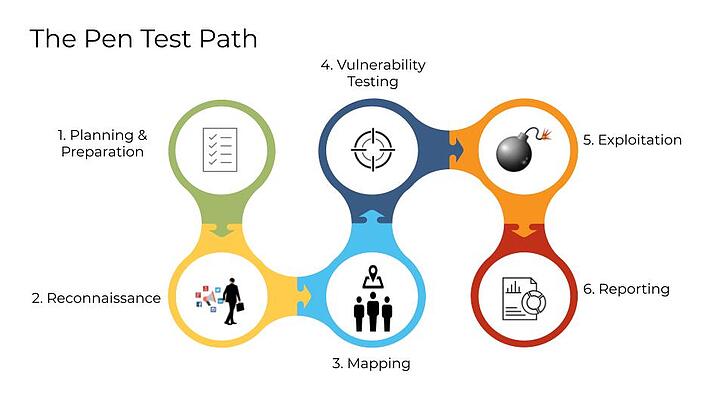
Steps for Conducting a Penetration Test
Conducting a penetration test is a crucial step in ensuring the security of any IT system or network. It involves simulating real-world attacks to identify and address security vulnerabilities before they can be exploited by malicious actors. While the process may seem daunting, it can be broken down into several key steps to ensure an effective and thorough assessment:
Establish Your Goals: Before embarking on the testing process, clearly define your objectives. Determine what specific information you aim to gain from the tests and how this knowledge will contribute to improving your organization’s security posture. These goals will guide your decisions and actions throughout the entire process.
Identify Vulnerable Points: Once your goals are established, take the time to identify all potential points of entry into your system or network that could be vulnerable to attack. This includes websites, databases, systems, and networks accessible over public networks or through remote connections like VPNs and SSH connections. It’s essential to consider both digital and physical entry points that attackers might exploit, such as open Wi-Fi networks or physical access points like doors.
Plan and Execute Tests: Develop a comprehensive test plan that outlines the specific tests and techniques to be employed. This plan should cover all identified vulnerable points and incorporate a variety of attack vectors. Conduct the tests, following the plan meticulously and leveraging both automated tools and manual methods to maximize the effectiveness of the assessment.
Challenges and Risks in a Penetration Test
While penetration testing is an invaluable tool for identifying security vulnerabilities and assessing an organization’s security defenses, it is not without its challenges and risks. It is crucial to consider and mitigate these factors to ensure a successful and ethically conducted penetration test.
One of the primary challenges is finding qualified personnel with the necessary expertise in multiple areas of information security. Effective penetration testers should possess knowledge and skills in computer networking, programming, database analysis, and web application development. They should also have excellent communication skills to effectively convey technical matters to clients and colleagues.
Another challenge is ensuring that the scope of the tests covers all relevant components of the target system or network. Comprehensive planning is essential to avoid overlooking any aspect of security during testing activities. Additionally, staying up-to-date with the latest tools and techniques used by hackers is crucial to ensure that no potential vulnerabilities are missed during the assessment.
Conclusion
Penetration testing plays a vital role in identifying weaknesses in systems and networks, enabling organizations to proactively address potential vulnerabilities before they are exploited by malicious actors. By simulating real-world attacks, penetration tests provide valuable insights into an organization’s security posture and help improve existing security measures. Through a structured approach that involves goal-setting, vulnerability identification, testing, analysis, and remediation, organizations can enhance their overall security and protect against security threats.